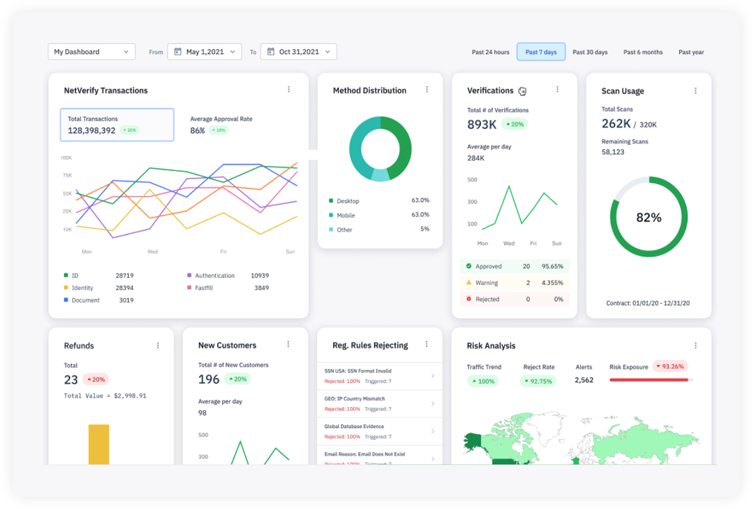
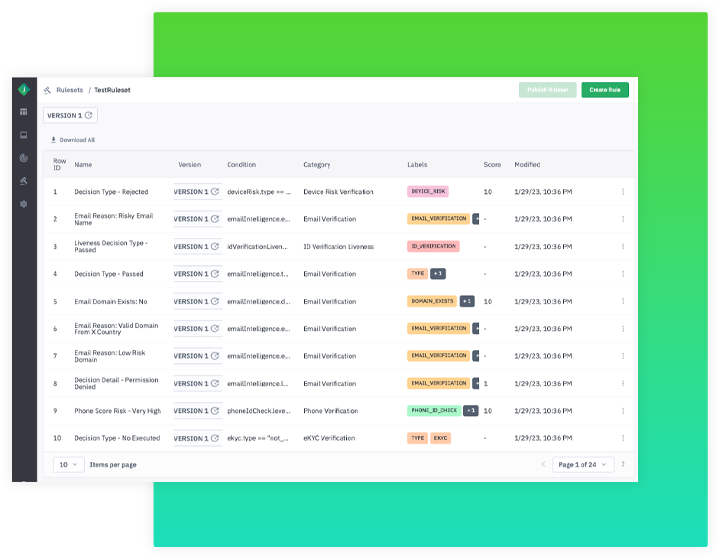
Whether reviewing real-time analytics, investigating transactions or updating rules, you can mitigate risk on your terms using our Unified Portal.


transactions processed
ID types in over 200 countries and territories
best-in-class global data sources
data scientists building cutting-edge Al and ML models

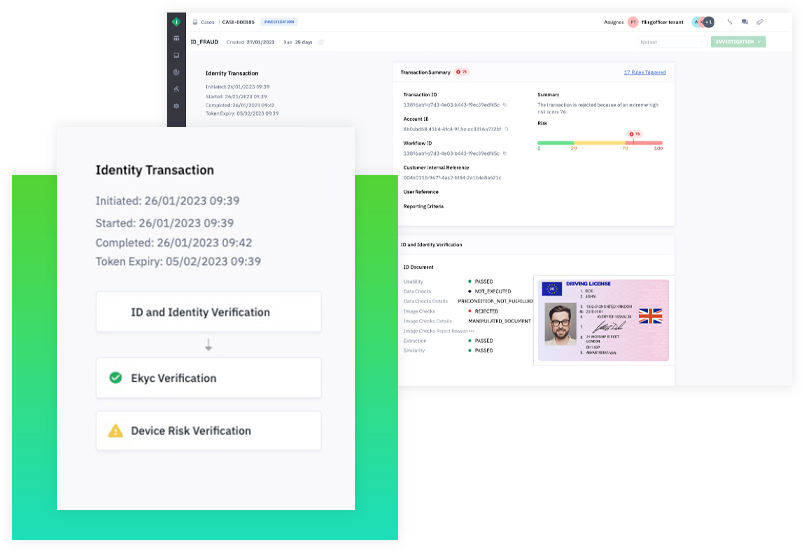
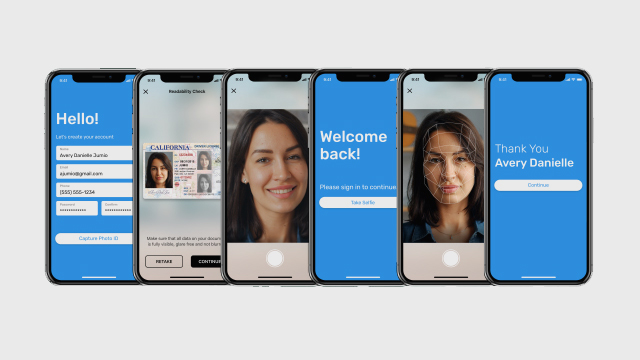
Verify identities and detect fraud throughout the customer lifecycle – from onboarding to ongoing monitoring.
Explore Identity Verification
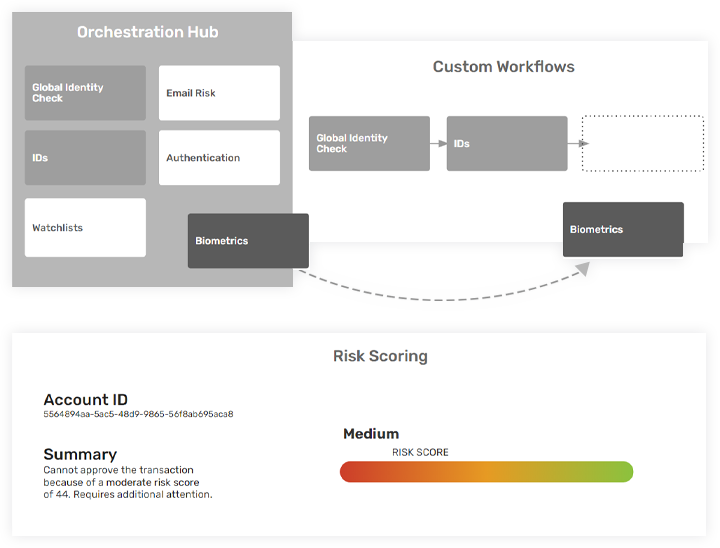
Gain predictive fraud insights and in-the-moment risk analysis based on past and present behavior data, along with recognized fraud patterns and risk signals.
Learn About Risk Signals
Deliver dynamic user experiences based on each customer’s verified identity and risk profile, allowing real customers to proceed without disruption.
See How It Works




Whether reviewing real-time analytics, investigating transactions or updating rules, you can mitigate risk on your terms using our Unified Portal.
This quick video shows how Jumio can help you:






"As Monzo continues to grow and pursue new markets, we know that Jumio will scale with our business and continue to provide an essential service – helping Monzo create the best-possible experience for our banking customers while fighting financial crime."
Head of Financial Crime, Monzo Bank
Read the Case Study

